CISCO Stealthwatch Free Training - FLOW - Soul of Stealthwatch - Lesson 3
In Cisco stealthwatch solution everything is based on flow, so I think flow is the soul of the system.
Flow is the trace of network conversation or in more technical language flow is a sequence of packet sharing the same properties that are sent between sending and receiving hosts. For example, when we download from an FTP server, packets sent from FTP server to PC, create a flow as they are part of the same conversation.
Please notice in the Cisco stealthwatch we do not packet analysis, instead we do flow analysis. In packet analysis we use packet capturing like "(R/ER)SPAN."
The packet analysis technique is suitable for the depth analysis of a specific conversation, but flow analysis is all about metadata. Flow analysis can help you with statistical purposes. Data like top talker or how much bandwidth is consumed by specific protocol or bandwidth usage.
NETFLOW
Netflow is a cisco proprietary used for flow analysis. main Netflow use cases are:
- bandwidth monitoring
- forensic analysis
- billing or accounting usage
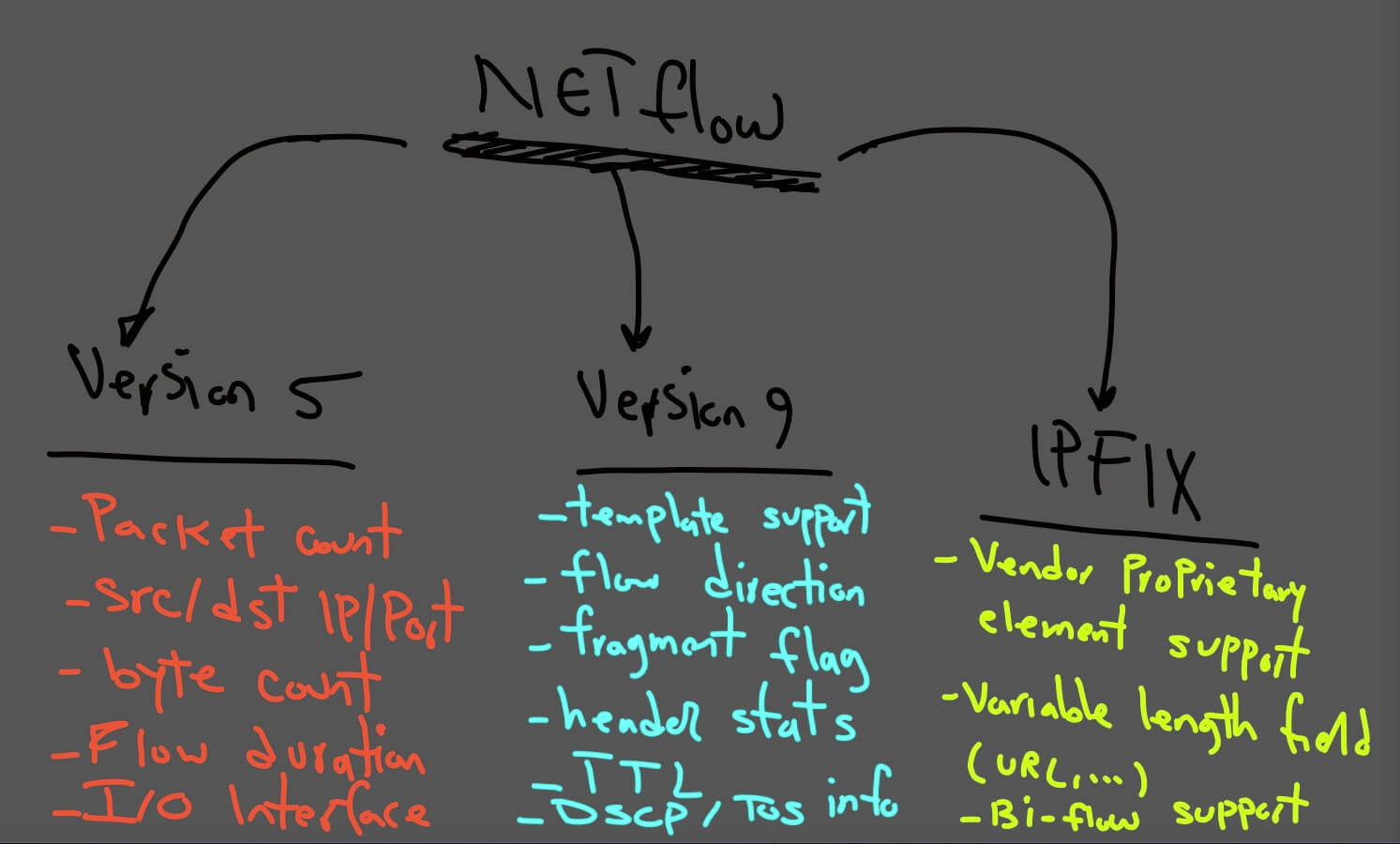
NETFLOW Versions
1. Netflow version 5
This version does not meet current needs, NetFlow version5 doesn't support ipv6 traffic, mac address, VLAN, or other extension fields. This version support essential information regarding traffic pattern,
Essential information like:
- Source/Destination IP and port
- Packet counts
- Byte counts
- Flow duration
2. Version 9
This version support:
- Template Support
- Numerous TCP flags/counters
- Flow direction
- Fragmentation flags
- ICMP and IGMP info
- Header stats
- Time-to-live
- DSCP/TOS info
- Destination routing info
3. Version 10 aka IPFIX
IETF standardizes IPFIX. Its extended version 9 that also supports variable-length fields. Example of the variable-length field is "HTTP hostname" or "HTTP URL" as well as enterprise- defined field.
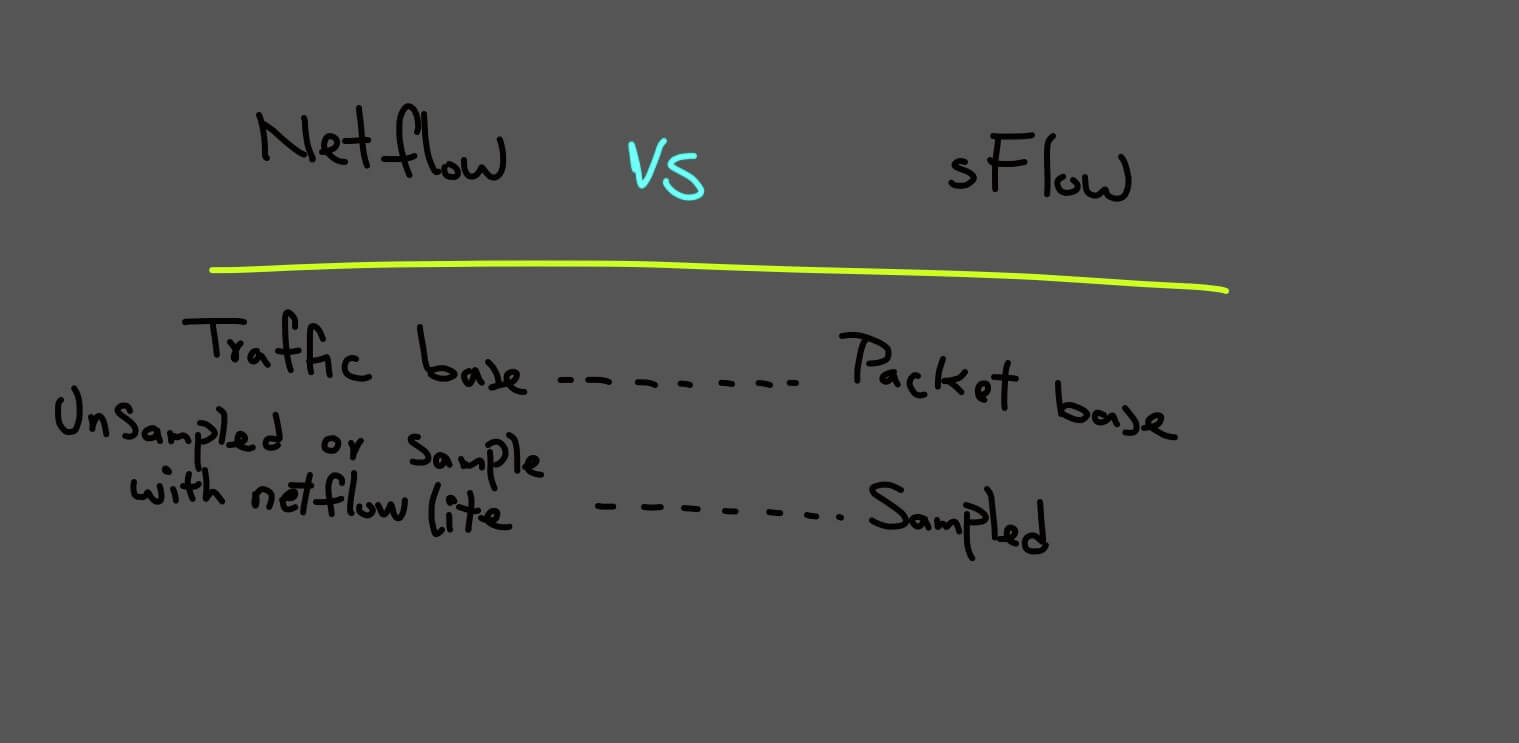
sFlow (sampled flow)
The goal of packet sampling and filtering is forward only certain packet.
In sFlow, we have a sampling rate. An average of 1 out of n packets is randomly sampled.
Netflow vs. sflow
Packet sampling is hardware-based and is performed by switching ASIC.
sFlow datagrams are continuously sent across the network in real-time, while the export of NetFlow records depends on active/inactive timers.
It makes sFlow good at massive DoS attacks detection, as the sampled network patterns are sent on the fly to the sFlow collector.
SFlow can monitor L2-L7 headers; the ability to monitor L2 headers (MAC, VLAN ID) has been added to NetFlow v9.
sFlow is only an approximation of the real traffic because sampled packets do not reflect all network traffic.
Based on this information sflow is not an option for forensic investigation.
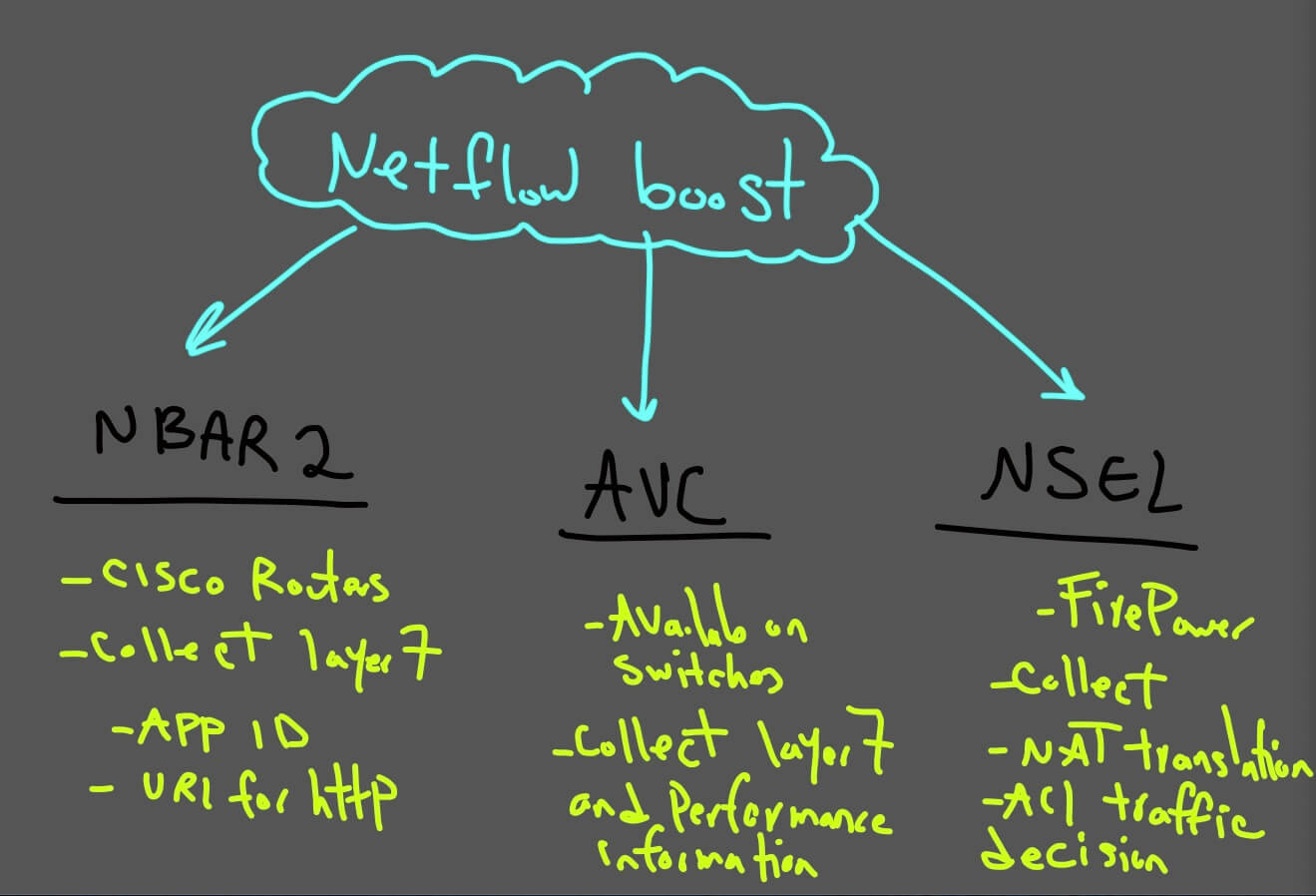
Netflow Boost
You can see in the diagram below how Netflow is boosted :)
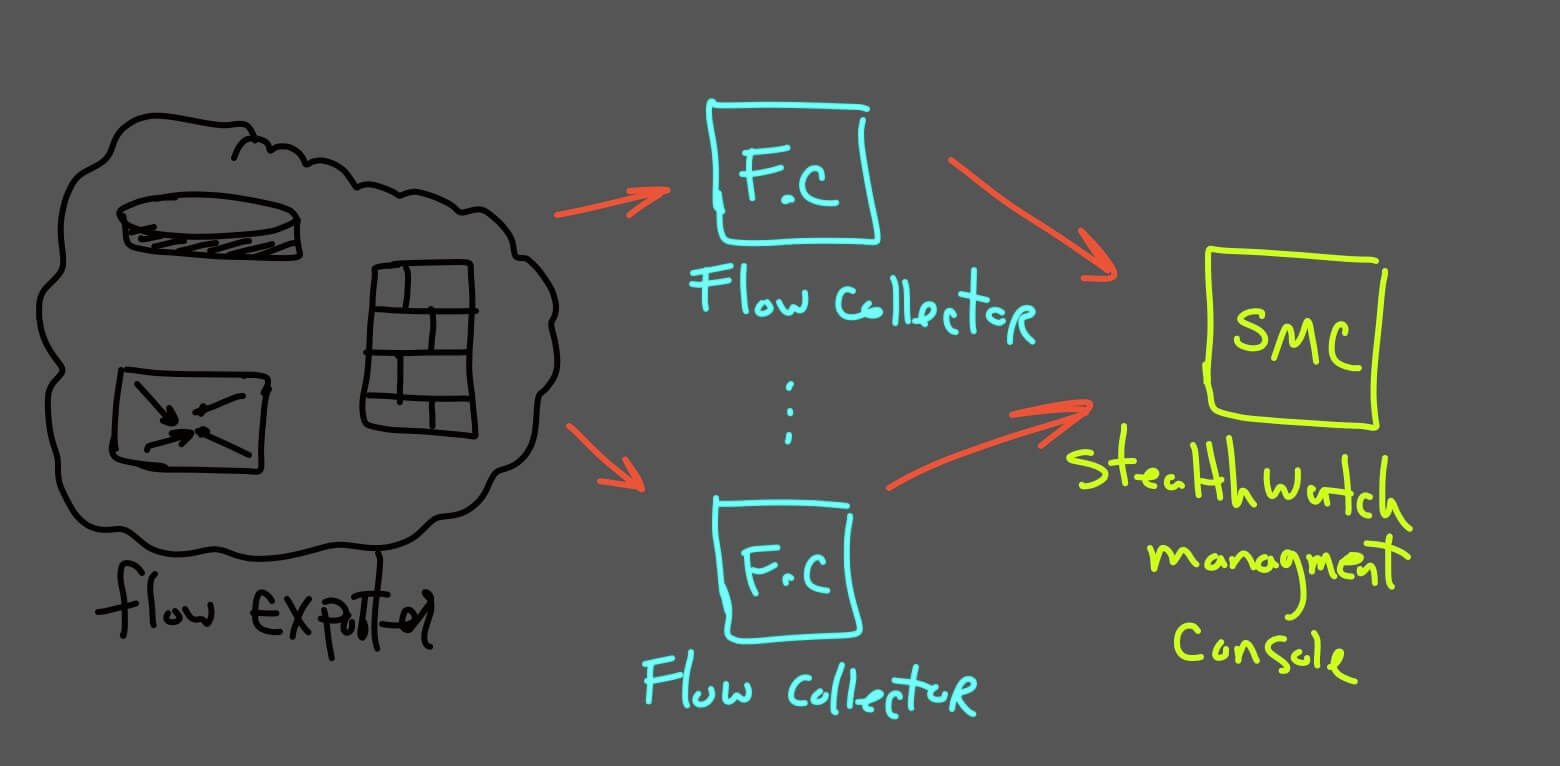
Netflow architecture components
- Netflow Exporter
- Netflow collector
- analysis application
How to configure NetFlow
In the next diagram, you can see how NetFlow should be configure:

In the next episode, I will start configuring NetFlow(IPFIX) on different devices like Firepower, catalyst 9300 , router 2911, CSR, and also switch 2960-x.
You will see different syntax and some limitations on them and also will talk and configure cisco about Cisco stealthwatch best practices.
See you soon!
